As cyber risks increase with COVID-19, directors must ensure they're across cyber attack issues and beware of false assurances, writes Alice Williams FAICD.
The frequency and cost of cyber attacks has increased exponentially during the past 10 years. It is predicted that cybercrime will cost the world US$6 trillion annually by 2021, up from US$3 trillion in 2015. It will be more profitable than the global trade of all major illegal drugs combined, with more than 800 websites sharing stolen information on the dark web.
The World Economic Forum Global Risks Report of 2019 identified data fraud/theft and cyber attacks as two of the top five global risks. The COVID-19 pandemic has further heightened these risks, with most employees and third-party suppliers working from home on systems with variable security arrangements.
Interpol’s COVID-19 Cybercrime Analysis Report, released in August, revealed a significant target shift from individuals and small businesses to major corporations, governments and critical infrastructure. “Increased online dependency... is also creating new opportunities, with many businesses and individuals not ensuring their cyber defences are up to date,” said the report.
Well-resourced “nation-state actors” (individuals working for a government to disrupt or compromise target governments, organisations or individuals to gain access to data or intelligence) and international crime organisations are seeking to capitalise on this uncertain environment. There has been a shift from military hardware to a global information war and companies need to proactively manage risks.
Cybersecurity governance
As a fundamental aspect of risk management, boards should regularly undertake reviews of cyber risk governance.
Key aspects to be covered in a cyber risk review include:
- Develop an understanding of the critical business systems, networks and data.
- Triage risk appetite based on the CIA triad model. This assesses risk on the basis of three elements of cyber risk — risks to confidentiality, integrity and availability of systems, networks and data.
- Develop an understanding of the key threat actors for your industry and company.
- Review the governance framework for the management of cyber risks.
- Assess the cybersecurity culture of the company.
- Assess leadership roles in the cybersecurity governance framework.
- Undertake regular staff training on cyber risk. This includes phishing and distributed denial-of-service (DDoS) exercises requiring full system back-up, recovery and working from the remote Disaster Recovery Plan (DRP)/Business Continuity Plan (BCP) site.
- Review third-party service provider arrangements and contractual obligations for cyber risk management and response.
- Review software as a service (SaaS) and cloud service provider contractual arrangements regarding cybersecurity.
Data commodity
Data is an asset the World Economic Forum has called the world’s new natural resource, providing a basis for competitive advantage and transforming industries. Companies are increasingly reliant on technology — an environment ripe for cybercrime.
Think about these example factors: the collection of sensitive/valuable data; reliance on multiple third-party suppliers; the Internet of Things; the current work-from-home environment. Boards have an obligation to assess sources of risk, risk controls and mitigation measures. As a consequence, many board risk registers have incorporated cyber risk as a key corporate risk, with an inherent risk rating of high to extreme. Once companies undertake risk-mitigation actions, the residual risk still tends to be high, as it is extremely difficult to mitigate cyber risks given the disproportionately large surface area that companies seek to protect and the online connectivity of operational systems.
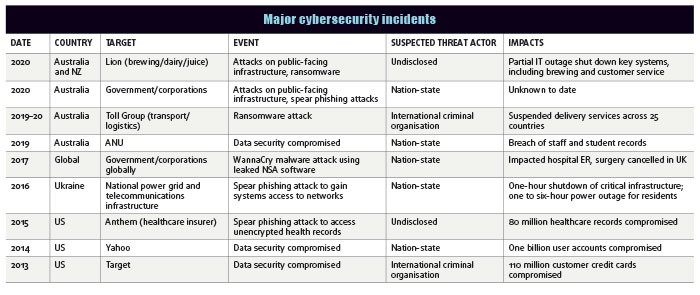
The transition to outsourcing and extension of supply chains can result in companies having a high reliance on digitally connected third parties for services. These third-party suppliers often have access to corporate systems and data, which creates another avenue for cybersecurity risk. The 2013 hack of US retailer Target is a one example. An international criminal organisation accessed the company’s payments system via an air-conditioning subcontractor’s systems access. Around 110 million customers’ credit card details were compromised through a memory-scraping malware attack. Target incurred more than US$150m in remediation costs as a result. The industries most at risk of cyber attack tend to be those with valuable, internationally tradeable data, critical infrastructure, and vulnerable open systems architecture.
Equally, boards should not discount insider threats, given the capacity for employees and contractors to move relatively undetected within systems. Edward Snowden’s release of sensitive National Security Agency (NSA) material in the US is a good example. Snowden had administrative access privileges, which enabled him to have relatively free access across all sensitive data. Following the breach, the NSA undertook a privilege audit and revoked 90 per cent of users’ high-level access powers.
Cybersecurity obligations for companies, directors and management are high from a legal and regulatory perspective — particularly with regard to the security and privacy of data, and breach reporting requirements. Companies that do not report breaches to affected parties and regulators in a timely manner face fines and risk severe reputational damage. This damage can be pervasive, impacting a company’s brand, customer loyalty and, ultimately, a listed company’s share price and credit rating. For example, Yahoo’s valuation in its merger with Verizon was reduced by US$350m following the 2014 security breach of more than one billion customer records by an alleged nation-state actor.
Key risk management strategies
- Audit employees’ IT systems privilege access. Use the least-privilege principle — only provide employees with password access to systems/data they require for their specific job responsibilities; and limit administration access privileges. Employee awareness training on company and industry specific cyber threats.
- Review cybersecurity expertise within the organisation — does the skill set match the company’s needs and inherent risks?
- Assess integration of physical security and cybersecurity across the organisation.
- Ensure systems restoration procedures are regularly updated and tested as systems and networks evolve.
- Ensure third-party providers have contractual obligations for cybersecurity, including breach reporting obligations that meet the company’s legal requirements. Transparency is maintained by those with access to your systems and where the data is domiciled.
- Cloud service provider contracts must include termination provisions that specify data transfer arrangements and proof/certainty of data destruction.
- Cybersecurity spend should represent about eight per cent of overall IT budget. IT security is a corporate asset.
- Assess the adequacy and appropriateness of cyber risk insurance and how this cover interacts with broader corporate insurance policies.
Strategies collated from Australian Cyber Security Centre, NYU, Harvard, US Department of Defense.
Skill base
Historically, boards have tended to comprise individuals with deep experience in law, finance and accounting, as well as former CEOs with broad commercial experience. Boards have typically viewed cybersecurity as an IT responsibility and relied on advice from the company’s chief information officer and assurances from external IT specialists on technology related matters.
Boards do not necessarily need to include IT professionals among their ranks, but as a consequence of the accelerating frequency of cyber attacks and cybercrime, directors need greater depth of understanding of these risks. The fourth edition of the ASX Corporate Governance Council’s Corporate Governance Principles and Recommendations highlights the requirement for directors to regularly assess the skills, knowledge and experience required to deal with new and emerging business and governance issues. Cybersecurity should be one of these key issues.
Professional development opportunities range from formal tertiary courses to webinars offered by major accounting and consulting organisations. This further education will enable directors to explore the subject of cybersecurity and ask probing questions. In instances where a cyber incident or breach has occurred, directors will be equipped to review material outlining the incident, understanding if fraud or a breakdown of an entity’s risk controls has occurred, and the lessons learned.
Beware of false assurance
Companies often seek to test the robustness of cybersecurity systems through periodic penetration-testing exercises, and use external technical experts to undertake the test. However, assurance gained through ad hoc penetration-testing exercises is insufficient and can lead to a false sense of cybersecurity assurance. Because penetration testing is periodic, it only incorporates a limited number of scenarios across what can be a very large digital surface area — and it does not tend to involve a whole-of-company response.
Protection is offered by antivirus software, but it is critical this software is updated in a timely manner. The cyber attack of the UK National Health Service (NHS) in 2017 is an example of the consequences of poor software patching. The NHS could not undertake medical procedures due to a Microsoft patch not being updated on release and computer systems being inoperable due to a malware attack. However, there are limitations with antivirus software as it is only effective for known viruses and malware threats. Given the constantly evolving cyber-threat landscape, antivirus software is always playing catch-up with threat actor approaches, so timely patching cadence is crucial.
Firewall selection and configuration may also be false assurance because it may not adapt to create appropriate boundaries as the complexity of the networks and systems grow. Assurance may also be gained through data encryption, but this must be applied to data at rest, in motion and in use, and regularly reviewed for currency and security.
In this high-risk environment, management and directors need to be acutely aware of the risk of cyber attacks. Every cyber attack, major or minor, should be investigated. Often, a minor cyber breach is a precursor to a more significant attack as they enable low-lying systems access over an extended period of time, allowing cybercriminals to develop an understanding of systems architecture prior to a major cyber attack or data breach. The risks to a company’s brand, customer relationships, regulatory penalties and market capitalisation of a major cyber attack can be material — active oversight is the best risk mitigant. As former ASIC chair Greg Medcraft stated at the World Economic Forum in 2017, “[Cybersecurity] preparedness must be a long-term commitment that has to be embedded in a company’s very culture.”
In July, the federal government announced a $1.35b Cyber Enhanced Situational Awareness and Response package to support key recommendations of its Cyber Security Strategy.
Alice Williams FAICD is a former Foreign Investment Review Board member and a director of Cooper Energy, Djerriwarrh Investments and Equity Trustees.
Latest news
Already a member?
Login to view this content

